In my previous post, Exam 70-410 Objective 5.2 - Create and Manage AD Users and Computers, we dealt with creating and managing AD Users and Computers which are one of the most critical objects in the domain. You can read about it here.
I have also created an entire page dedicated to the 70-410 exam series, Microsoft Windows Server 2012 R2 Exam 70-410 - Installing and Configuring
In today's objective, we will be looking at the following:
- Create, Copy, Configure and Delete Groups and OU's.
- Configure Group Nesting.
- Enumerate Group Membership.
- Convert Groups.
- Manage Group Membership using Group Policy.
- Delegate the creation and management of AD objects.
- Manage Default AD containers.
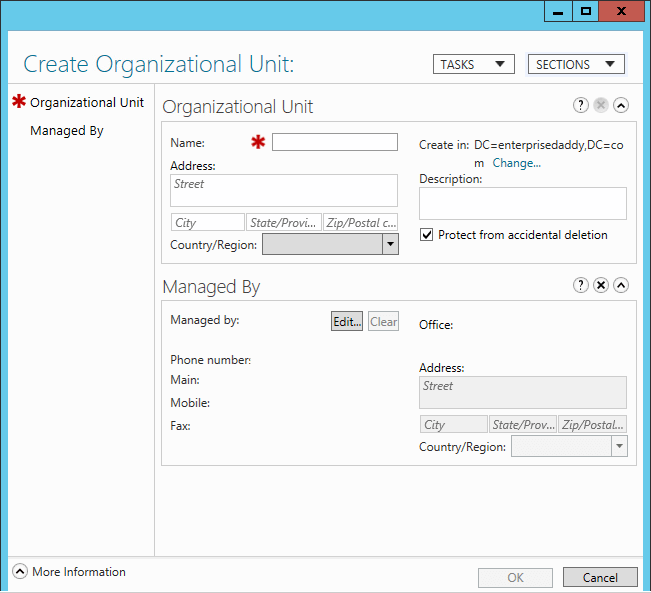
Create, Copy, Configure and Delete Groups and OU's
As seen earlier with Users and Computers, there are various ways that you can create AD objects.
It really comes down to your personal preference or habits that you have built over a period of time, some people must find it easy using the GUI tools and some may like to use PowerShell for its ease.
Using Active Directory Administrative Center
Using Active Directory Users and Computers
Using Command Line
The syntax for creating a group can be seen below. For more information, click here.
dsadd group <groupDN> [parameters]
Using PowerShell
The cmdlet that creates a new group is New-ADGroup
I will show you the general syntax used while creating the group, but I highly recommend you go through the help files to understand the various ways that you can use this cmdlet.
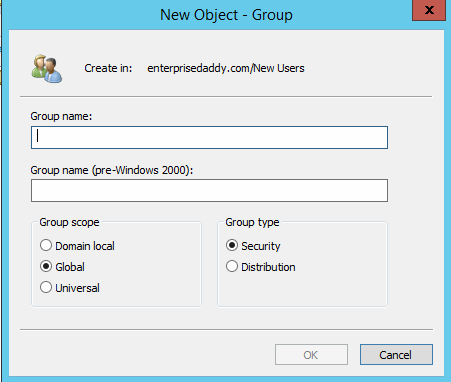
New-ADGroup -Name <GroupName> -SamAccountName <samAccName> -GroupCategory Distribution|Security -GroupScope DomainLocal|Global|Universal -Path <distinguishedName>
We need to look at two important parameters before we proceed any further, GroupCategory and GroupScope.
Group category defines what kind of group it is going to be, either Distribution or a Security Group.
Group Scope defines the purpose of the group, the three available options are Domain Local, Global, and Universal.
I have a detailed article, explaining the categories and scopes which are can refer below.
How to Create Active Directory Groups using PowerShell
Configure Group Nesting
Group Nesting is the term used when groups are added as members of other groups.
As we saw the previous section, the various group scopes available at our disposal were Domain Local, Global and Universal types.
While configuring Group nesting, we need to understand the AGUDLP process.
AGUDLP standards for
A - Accounts
G - Global Groups
U - Universal Groups
DL - Domain Local Groups
P - Permissions
Advantages of AGUDLP
Allows administration to be divided up between different administrators in the forest. Administrators can have control at the forest level or control can be separated at the domain or resources level.
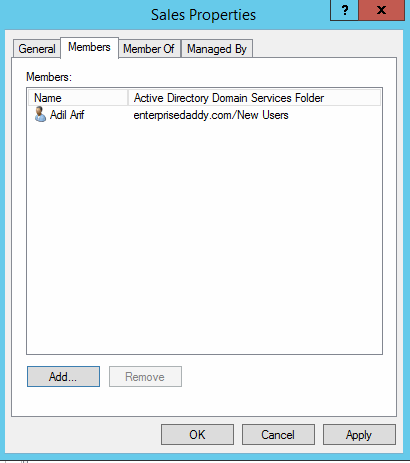
Enumerate Group Membership
There are various ways that you check the members of a group.
Open up a Group from Active Directory Users and Computers, Right click and select Properties, click on the Members tab.
Using PowerShell also, you can check the membership of a Group.
The cmdlet that you would use is Get-ADGroupMember
Some time back, I wrote an excellent article about finding out Membership details using PowerShell, which you can find below.
Find Group Membership using PowerShell
If you are curious to know more, I also wrote an article on how to bulk remove users from multiple groups using PowerShell as it can be tedious using the GUI.
How to Remove Users from Groups using PowerShell
Convert Groups
We saw the different that are available to us, now let us see if in case we need to change the group scopes.
| Type | To Domain Local | To Global | To Universal |
| Domain Local | NA | Not permitted | Permitted only when the Domain Local group does not have other Domain Local groups as members. |
| Global | Not permitted | NA | Permitted only when a global group is not a member of another global group. |
| Universal | No restrictions | Permitted only when Universal group does not have any other Universal groups as members. | NA |
Manage Group Membership using Group Policy
It is also possible to control group memberships by using Group Policy.
When you create Restricted Group Policies, you can specify the membership of the group and enforce it, so that changes made to the membership will be revised during the next policy refresh.
I have written an article previously, which you can find below.
How to add Domain Local Users to Remote Desktop Users group using Group Policy
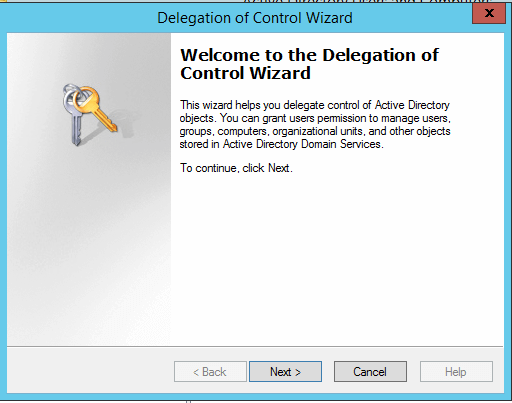
Delegate the Creation and Management of AD Objects
Creating OU's enable you to implement a decentralized administration model, in which others manage portions of ADDS hierarchy, without affecting rest of the structure.
Delegating Authority at a site level affects all domain and users within the site.
Delegating Authority at the domain level affects the entire domain.
However, delegating authority at the OU level affects the OU and its subordinate objects only.
To delegate, right click on OU > Open Delegate Control Wizard.
Advantages of Delegation:
- A minimal number of administrators with global privileges.
- Limited scope of errors.
Manage Default Containers
There are several container objects that are installed by default when you promote the first domain controller on your network.
They differ from manually created containers because their object attribute type is literally named a container. They don't have the same properties as other generic Active Directory containers (such as sites, domains, and OUs).
You cannot delete them nor can you create new objects of that container object type. You can also not associate Group Policy Objects with these. These containers are:
Computers - All member servers in the domain are placed, by default, in the Computers container. Additionally, all workstations joined to the domain also appear in this container.
Users - Much like how Computers and Servers joined to the domain are auto-dumped into the Computers container, Users of all levels are automatically placed inside the Users container.
To get over this, we can use redirect the users and computers to the desired OUs for future objects.
redirusr "ou=New Users,dc=enterprisedaddy,dc=com"
Redirects all the new user objects that are added to the Domain to the New Users OU.
redircmp "OU=New Computers.dc=enterprisedaddy,dc=com"
Redirects all the new computer objects that are added to the Domain to the New Computers OU.
This completes the Exam 70-410 Objective 5.3, I hope that this has been informative and thank you for reading! 🙂