Hello fellow system admin,
Welcome to the 70-410 Exam series, in our last post, we covered configuring Group Policy Objects wherein we saw the basics of Group Policy Objects, Starter GPO's, GPO links and configuring a central store.
Continuing on the same path, in today's post, we will be looking at Configuring Security Policies.
The various objectives that we will be looking at are:
- Configure local Users and Groups.
- Configure User Rights Management.
- Configure Security Options Settings.
- Configure Audit Policy.
- Configure User Account Control.
- Configure Security Templates.
Explaining the security policies is going to a little cumbersome, so we are going to take some use cases and try to understand how the security policies are configured using the Group Policy.
Below are the requirements that we need to fulfill by the end of this article.
- Disable local built-in administrator and replace with localadmin user.
- Add IT group to administrators.
- Grant ITBackups group rights to perform remote backups.
- Enforce machine lock after 15 minutes of inactivity, and display user information once the session is locked.
- Audit logon and account logon failure events.
- Audit removable storage.
- Enforce UAC for administrators and remove OTS (Over the Shoulder) elevation prompt.
- Disable UAC for software installations.
Configure local Users and Groups
To configure this, we will be looking at the following use cases.
- Disable local built-in administrator and replace with localadmin user.
- Add IT group to administrators.
First, we will create a new GPO called Security GPO and link it to the NewComputers OU.
Now, go ahead and Edit the GPO and go the following location.
Computer Configuration > Preferences > Control Panel Settings > Local Users and Groups.
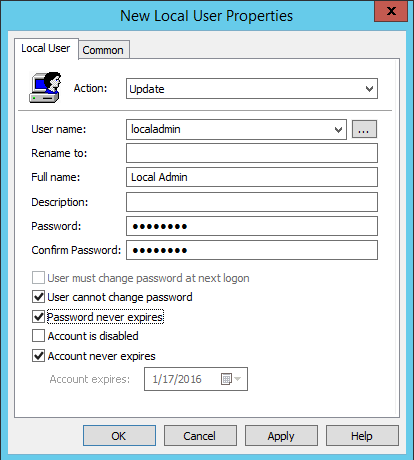
As per our requirements, we will first need to create a new user called "localadmin", Right Click and create a new user.
Give the User Name as localadmin and provide a password, also, make sure to that the user cannot change the password and the password never expires as this is going to be an important account on every computer.
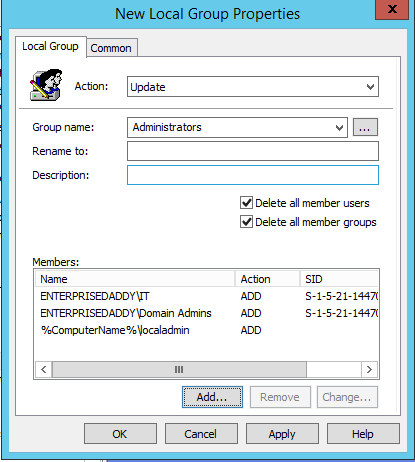
Next up we need to add the IT group to the Administrators group along with the localadmin account.
Therefore, we need to create a new local group and perform the below.
Make sure to delete any existing users and groups and selecting the check boxes.
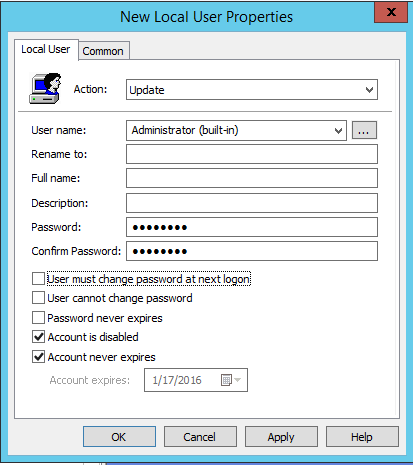
The final step is to disable the built-in Administrator account. To do so, create a new user and select the built-in Administrator account from the dropdown and disable the account as seen below.
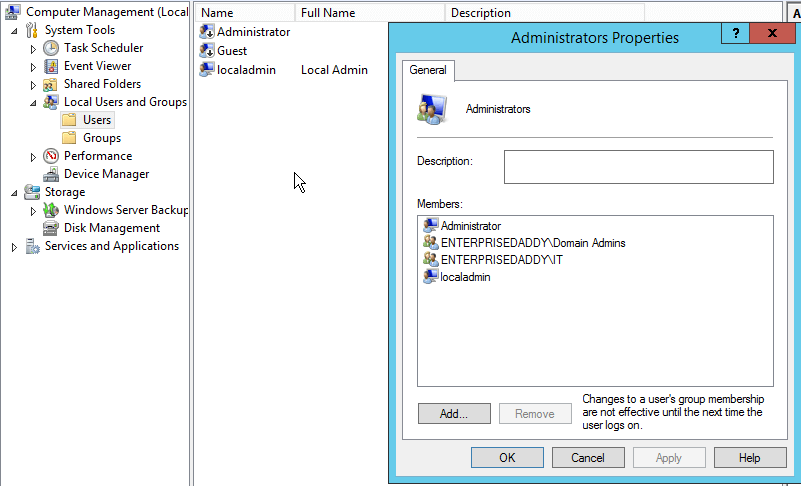
Now to confirm if the settings are applied as part of the Group Policy, login to a member server and check the local Users and groups.
Type the below so that the group Policy refresh happens immediately rather than the normal cycle that it takes.
gpupdate /force
You can see below that the localadmin account is created and added to the Administrators group along with Domain Admins and IT group.
And the Administrator account is also disabled.
Configure User Rights Assignment
For this section, we will be looking at the below use case.
- Grant IT Backups group rights to perform remote backups.
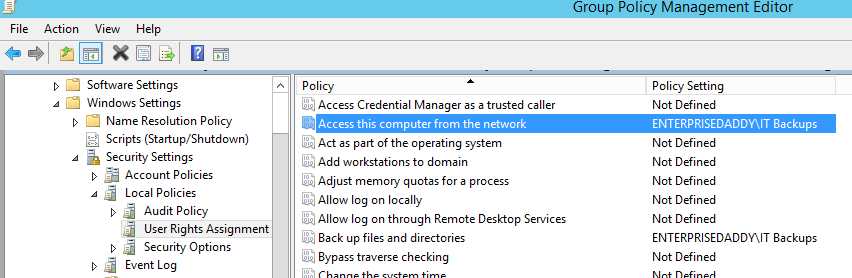
For the same Security GPO, go to Computer Configuration > Windows Settings > Local Policies > User Rights Assignment
Enable the below and add IT Backups group.
- Backup Files and Directories.
- Access computers from the network.
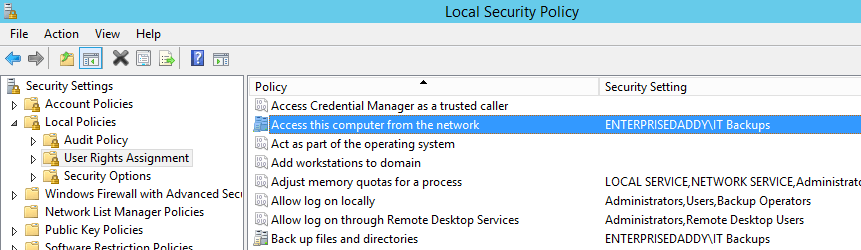
To verify, login to the member server and check the Local security policy section to see if the policy has applied.
Configure Security Option Settings
To perform this activity, we will be looking at the below use case.
- Enforce machine lockout after 15 minutes of inactivity and display user information once the session is locked.
Edit the same Security GPO and navigate to the below location.
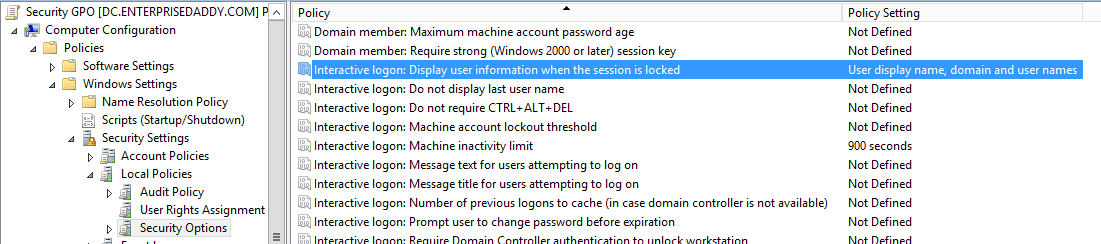
Computer Configuration > Windows Settings > Local Policies > Security Options and set the values for the settings as seen below.
- Machine inactivity limit: 900 seconds
- Display User information: User displayname, domain and user names.
Configure Audit Policy
For this section, we will be configuring the below use cases.
- Audit logon and account logon failures.
- Audit removable storage.
To do so, edit the Security GPO and navigate to the following location.
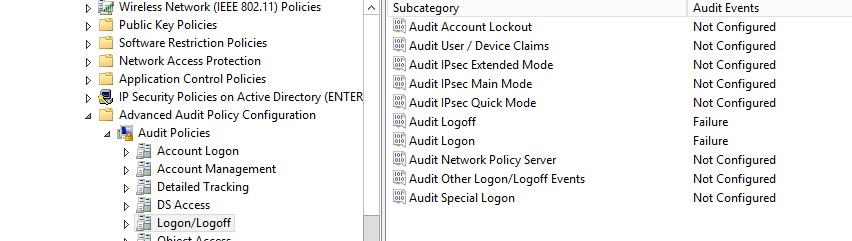
Computer Configuration > Windows Settings > Advanced Audit Policy Configuration > Audit Policies and enable the below.
- Account Logon > Audit Credential Validation > Failure.
- Logon/Logoff > Account Logon > Failure.
- Logon/Logoff > Account Logoff > Failure.
- Object Access > Audit Removable Storage > Success, Failure.
Configure User Access Control
To explain this section, we will be looking at implementing the below settings.
- Enforce UAC for administrators and remove OTS elevation prompt.
- Disable UAC for software installations.
To do so, navigate as below.
Computer Configuration > Windows Settings > Local Policies > Security options and the select the following options.
-
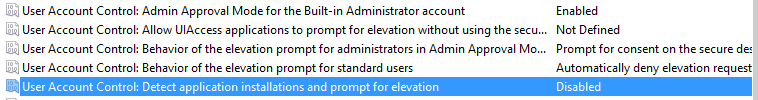
Behaviour of the elevation prompt for administrators in Admin approval mode: Prompt for consent at the secure desktop.
- Built-in Admin account: Enabled.
- Behaviour of the elevation for standard users: Automatically deny elevation requests.
- Detect application installations: Disabled
Configure Security Templates
A security template is a collection of configuration settings stored as a text file with a .inf extension.
Security templates can contain many of the same security parameters as GPO's.
The setting that you can deploy by using security templates includes many of the security policies covered in this objective, including audit policies, User rights assignments, security options, event log policies and restricted groups.
That is all for we have for today, I hope this has been informative and thank you for reading!




5 Comments
Hi,
I need to give exam for 70-410, if you could give me related dumps then it will be greatful for me.
Hi Purbita,
I am afraid that I do not have any dumps and I believe that it will not help you understand the technology. You may pass the exam but I think you are better off without it.
Thanks for your reply.
Hi Adil,
can you provide links for:
Objective 3.2: Create and configure Virtual machine storage.
Objective 3.3: Create and configure virtual machine networks.
Objective 6.3: Configure Windows Firewall
as I am preparing for the exam and everything so far have been great.
Very nice & quick informative