Welcome back,
In my previous post, we discussed on how to add an External Platform Services Controller or an Embedded vCenter Server instance to an Active Directory Domain.
Now, that we have the necessary accounts created in the AD Domain, let us go ahead and add Active Directory as Identity Source in VCSA 6.5 or vCenter Server 6.5.
What's the real use case of doing this? By default when you install an External Platform Services Controller or an Embedded vCenter Server instance, VMware creates an SSO Domain that is used to authenticate a user that he/she has access to in a vSphere Environment.
Now assuming that you have a large environment and you have many users that need access to the vCenter Server, you will have to consider adding Active Directory as Identity Source in VCSA 6.5.
Otherwise, imagine the pain of creating those accounts again in the SSO Domain, completely unrealistic and pain in the bottom!
This article explains how to add AD as Identity Source in vSphere 6.5 and how to get the "Use Windows session authentication" checkbox to work with the enhanced authentication plugin.
Log in to the vSphere Web Client using the SSO Admin account that was created during the installation of the External PSC or Embedded vCenter instance.
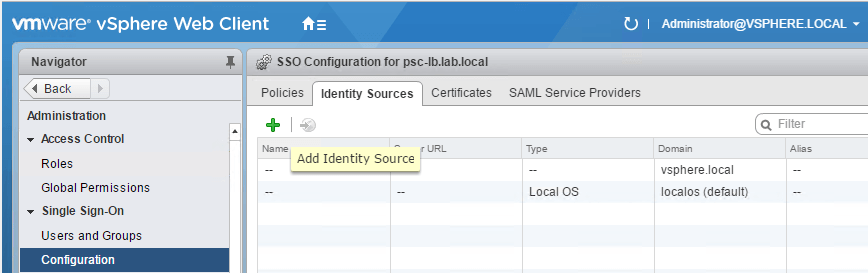
Navigate to Administration > Single Sign-On > Configuration. Select the Identity Sources tab and click on the + sign as seen below:
A wizard pops up and there are two types of options available:
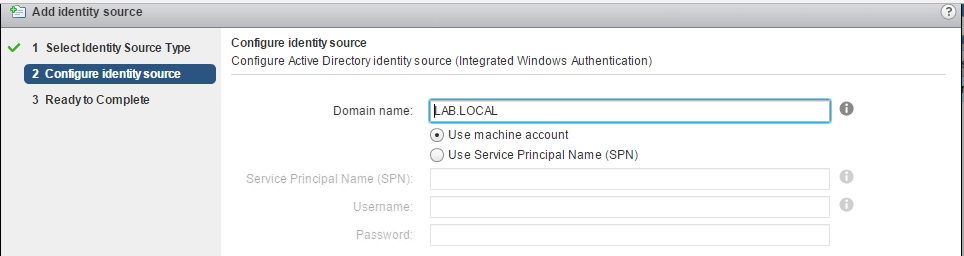
- Active Directory (Integrated Windows Authentication): This option works with both, the Windows-based vCenter Server and the vCenter Server Appliance. The underlying system has to be a member of the Active Directory domain.
- Active Directory as an LDAP Server: If the underlying system is not part of the Active Directory domain.
First, let us look at the options available for each type and what are the fields that need to filled when using each type.
For the Active Directory (Integrated Windows Authentication) method, there is no real information required other than the Domain Name of the Active Directory Domain.
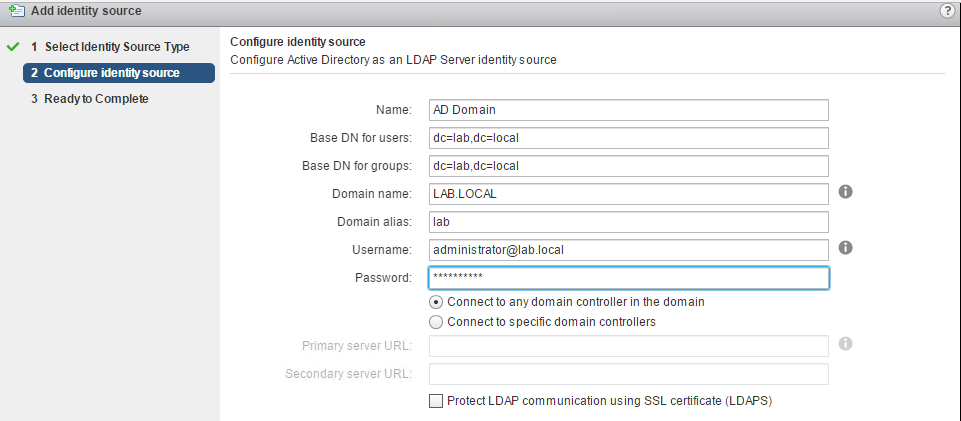
For Active Directory as an LDAP Server, below fields need to be added to successfully add AD domain as an Identity Source in SSO.
- Name: AD Domain (or anything that you really wish)
- Base DN for users: The Distinguished Name (DN) of the starting point for directory server searches. Example: If your domain name is lab.local the DN for the entire directory is "DC=lab,DC=local".
- Base DN for groups: The Distinguished Name (DN) of the starting point for directory server searches.
- Domain name: Domain name. Example: "lab.local"
- Domain alias: NetBIOS name. Example: "lab"
- Username: In my case, I have provided the administrator account of the AD Domain.
Click Next and finish the configuration wizard.
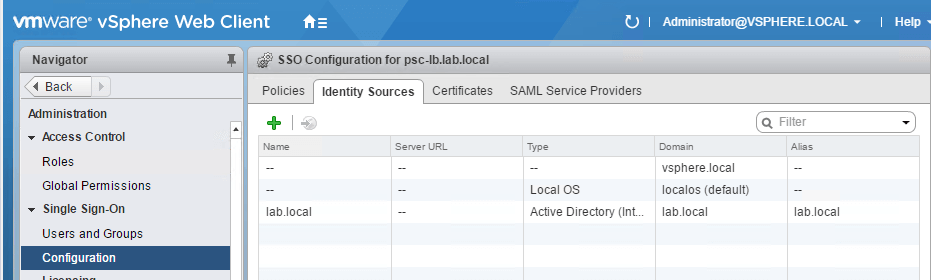
Now, the AD Domain should be listed under the Identity Sources tab as seen below.
If you notice, I selected in the First option Active Directory (Integrated Windows Authentication) to create the Identity Source.
For an AD user to be able to access the vCenter Server, we need to first set permissions on the vCenter in order to be able to access a certain part of the vCenter Server.
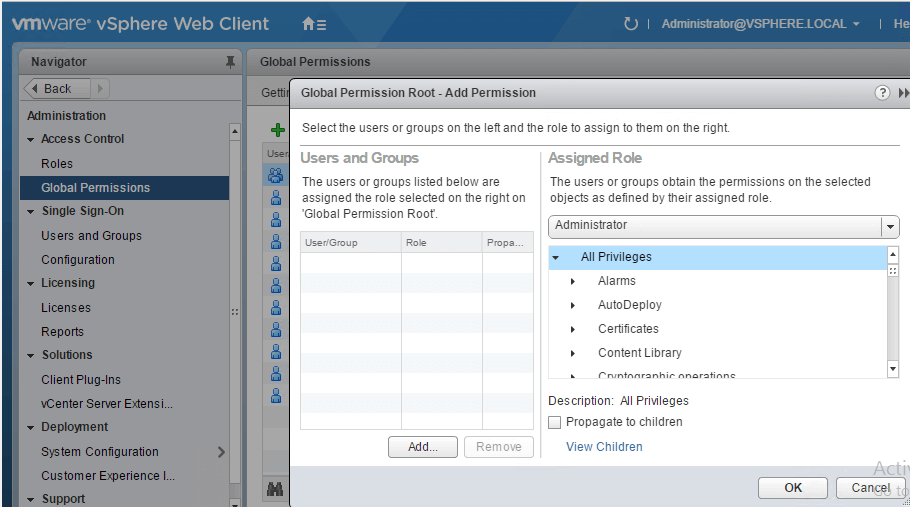
In our example, we will assign a Global Permission to an AD user account of Administrator role. Navigate to Administration > Access Control > Global Permissions. Click on the + symbol to add a User.
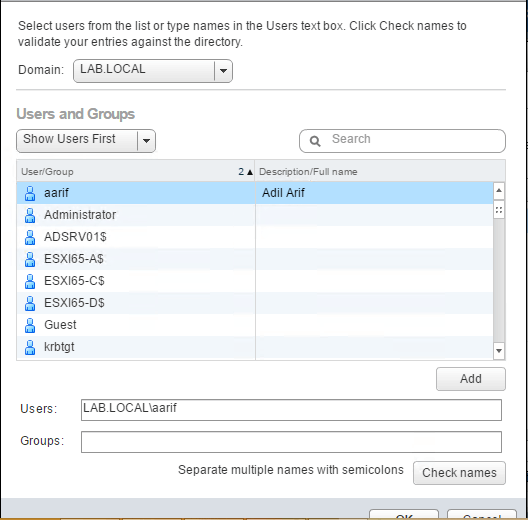
Click on Add, select the Domain as Lab.local and select the User that needs to be added, click on Add and click OK twice.
The above user account from AD should now be able to log in to the Web Client with Administrator Role on the vCenter Server.
I hope this has been informative and thank you for reading!




1 Comment
Nice Article Arif!!
Do you know of a way to do it Command line?