There were a lot of features that were introduced with the vSphere 6.5 and vSphere 6.5 Encryption of VMs was one among them.
I have written various articles on vSphere 6.5 which you can find here, but I had never written a post on vSphere 6.5 Encryption and I did receive a few requests asking if I could write a post on how to encrypt the VMs in a test environment.
Firstly to set up Virtual Machine encryption, we need a Key Management Server and the encryption of VMs is going to performed by the Key Management Servers.
At the time of writing this article, VMware supports four Key Management Servers, which are:
- SafeNet KeySecure
- Vormetric Data Security Manager
- HyTrust KMIP Server
- Thales KMS
For our testing purposes, we will be using a Docker container image created by William Lam and spin it up as a container.
Below are the commands that you will be running on the Dicker client. For folks, who are not familiar with Docker there are plenty of online resources available that you can refer to before trying this in your lab.
The first step will be to pull the Docker container image from the public repository using the below command.
docker pull lamw/vmwkmip
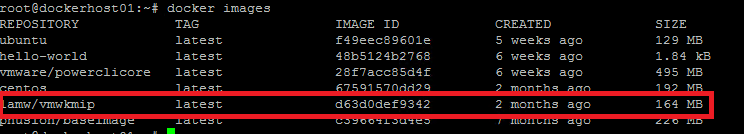
You can verify if the docker image has been downloaded to the docker host by running the command:
docker images
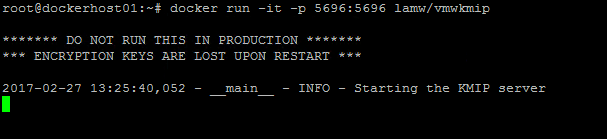
The second step to start the container using the below command.
docker run -it -p 5696:5696 lamw/vmwkmip
The above command starts the container using the image we pulled in the previous step and it exposes the maps the port 5696 on the host to the port 5696 on the container.
As you can see above that the container has started and there is a warning that states that this should be run in production since the keys used to encrypt VMs are stored in memory and will be lost upon reboot.
To exit out of the container, you need to press the Ctrl P + Q.
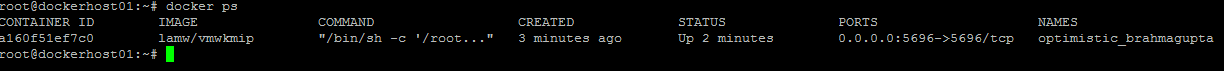
Run the below command to make sure that the container is running in the background.
docker ps
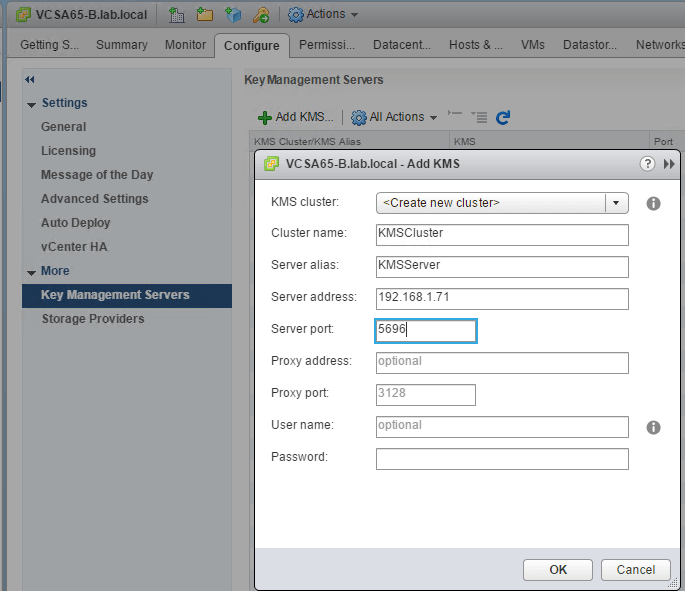
Now that we have everything is taken care of, let us log into the Web Client of the vCenter Server. Select the vCenter Server > Configure > More > Key Management Server > Add KMS
Add the details of the container that we created in the previous step and click OK.
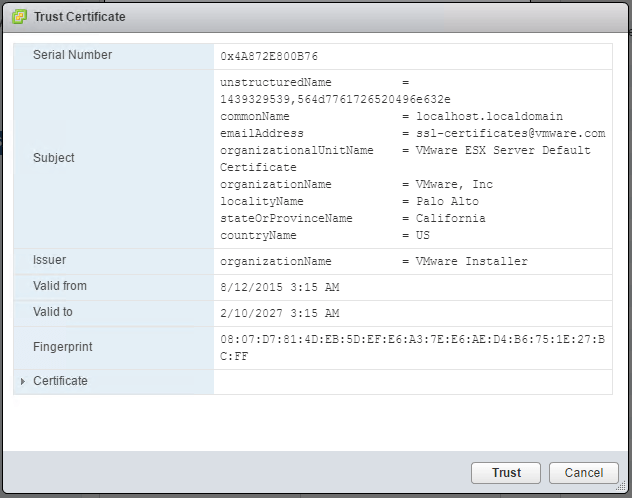
Trust the certificate as shown below.
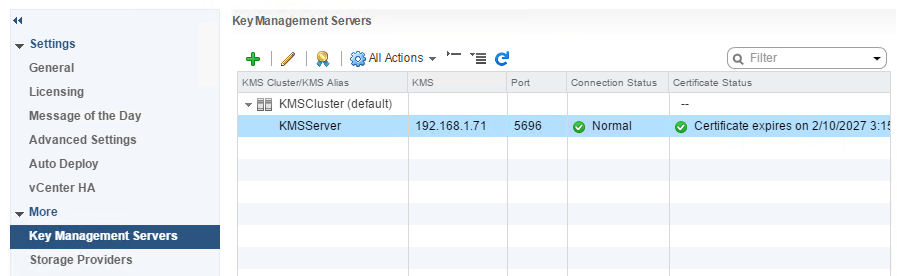
If you followed along correctly and everything was set up fine, you should see the below screen which shows Connection and certificate status as Green.
From here on, we should be able to apply the VM Encryption Policy that is created by default once the vCenter Server is installed.
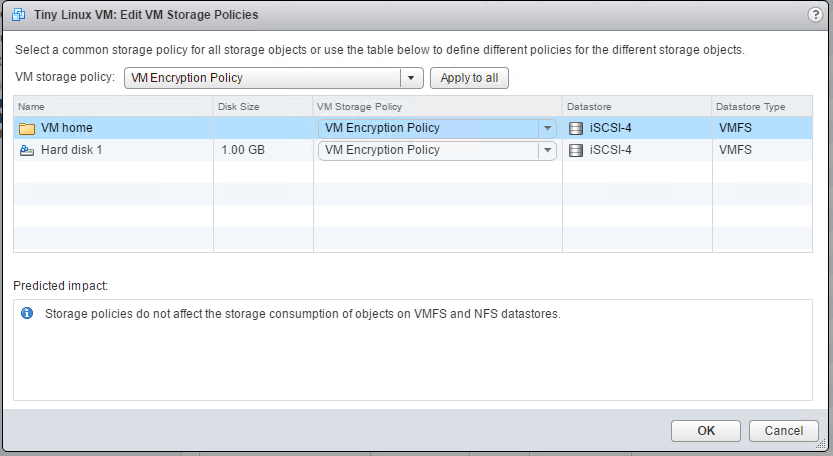
Right click on the VM > VM Policies > Edit VM Storage Policies. Select VM Encryption Policy from the drop-down and click on Apply to all. Click OK.
Note: The VM Policy can be applied when the VM is created. If the VM is already created, then power Off the VM and then apply the Encryption policy.
That's it! Now the VM configuration file and the VMDK's associated with the VM are all encrypted.
I hope this has been informative and thank you for reading!
Reference articles:
KMIP Server Docker Container for evaluating VM Encryption in vSphere 6.5




1 Comment
Very good topics, you have published in the web.
Thanks