I have been busy off late and haven't had the time to blog much, however, I am keeping myself updated with the latest news in the Azure Cloud space and I recently heard about Azure Update Management.
What is Azure Update Management?
It is a free offering from Microsoft in your Azure Automation account which can be used to manage Operating System Updates for your Windows and Linux Virtual Machines deployed in Azure, on-premises environment, or other cloud solution providers.
Think of it as a WSUS setup back in the day that everybody used to or still uses to manage their Operating System Updates in your IT infrastructure. But, WSUS is only available for Windows machines and cannot be used with Linux Machines, whereas Azure Update Management can be used with both.
What are the requirements for Azure Update Management?
In my opinion, there are only two major requirements for you to start using Azure Update Management, which are:
- Log Analytics Workspace: A workspace is essentially a container where log data is stored.
- Azure Automation Account: This account will be used to enable various capabilities in your workspace.
How does Azure Update Management Solution work?
Any computer that is managed by Azure Update Management uses the below configurations for performing assessment and update deployments:
- Microsoft Monitoring Agent for Windows or Linux.
- PowerShell Desired State Configuration (DSC) for Linux.
- Automation Hybrid Runbook Worker.
- Microsoft Update or Windows Server Update Services for Windows computers.
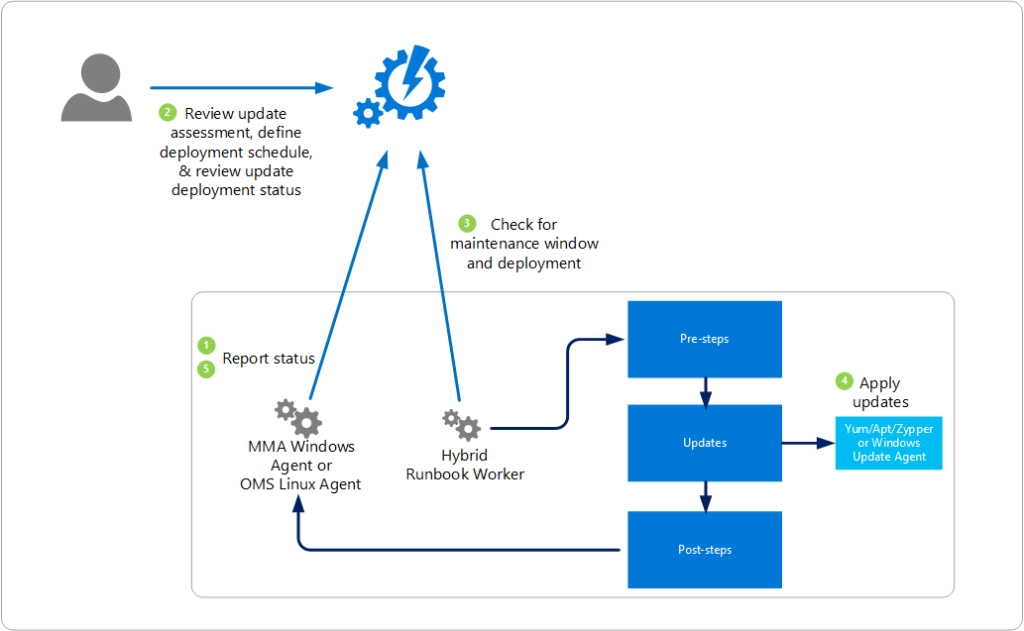
Below diagram explains the data flow on how the Azure Update Management solution assesses and applies updates to all Windows and Linux computers that are managed by the solution.
Now that we understand how Update Management assesses and applies the update. Let us look at how often the scans happen.
A Windows machine performs a compliance scan every 12 hours by default, whereas for Linux Machines perform a scan once in every 3 hours.
In addition to these regular scans, both Windows and Linux machines perform an additional scan within 15 minutes if the Microsoft Monitoring Agent (MMA) is restarted.
After a machine completes the update compliance, the logs are forwarded to Log Analytics Workspace (which is a requirement) by the MMA agent.
Once a CVE is released, it can take 2-3 hours for the patch to show up for Linux machines for assessment and for Windows machines, it can take 12-15 hours.
What components make up the Azure Update Management Solution?
There are two major components that are required for the Azure Update Management solution to work perfectly and they are:
- Hybrid Work Groups
- Management Packs
Hybrid Worker Groups
As mentioned earlier along with the Microsoft Monitoring Agent, the Azure Update Management solution also requires Automation Hybrid Runbook Worker to support the runbooks that are included in the solution for Windows machine. And it is automatically configured when the solution is enabled.
Each Windows computer that's managed by the Azure Update Management solution is listed in the Hybrid worker groups pane as a System hybrid worker group for the Automation account. The solutions use the naming convention Hostname FQDN_GUID.
Management Packs
If System Center Operations Manager management group is connected to a Log Analytics workspace, the below management packs are installed in Operations Manager. And these management packs also get automatically installed on the connected Windows machine.
- Microsoft System Center Advisor Update Assessment Intelligence Pack (Microsoft.IntelligencePacks.UpdateAssessment)
- Microsoft.IntelligencePack.UpdateAssessment.Configuration (Microsoft.IntelligencePack.UpdateAssessment.Configuration)
- Update Deployment MP
What are the Support/Unsupported client types?
On the Windows front, any server operating system running Windows Server 2008 R2 SP1 and later is supported. However, Windows Server 2008, Windows Server 2008 R2 RTM are only supported for update assessments.
For Linux machines, the various distributions that are supported are CentOS 6 (x86/x64) and 7 (x64), Red Hat Enterprise 6 (x86/x64) and 7 (x64), SUSE Linux Enterprise Server 11 (x86/x64) and 12 (x64), Ubuntu 14.04 LTS, 16.04 LTS, and 18.04 (x86/x64).
Any Windows client operating system and Windows Server 2016 Nano editions are not supported.
What are the networking requirements?
The below addresses are required for the Azure Update Management solution work properly and communication happens securely over port 443.
| Azure Public | Azure Government |
|---|---|
| *.ods.opinsights.azure.com | *.ods.opinsights.azure.us |
| *.oms.opinsights.azure.com | *.oms.opinsights.azure.us |
| *.blob.core.windows.net | *.blob.core.usgovcloudapi.net |
| *.azure-automation.net | *.azure-automation.us |
We have covered the introduction and overview of the Azure Update Management Solution and in the next post, we will look at enrolling Azure VMs into the solution.




1 Comment
Hi Adil Arif,
I have gone through the Azure Update Management articles and those are really good with enough information.
http://adil-arif.com/2018/11/azure-update-management-part-1-introduction-and-overview/