Kubernetes Secrets are objects which allow us to store and manage sensitive information, such as passwords, SSH keys, etc. They are similar to Kubernetes ConfigMaps, but ConfigMaps are used to store non-sensitive data.
The procedure of using Kubernetes Secrets is the same as ConfigMaps, so this post is going to look quite similar to ConfigMaps. First, we will create the secret and then we will inject it into the pod.
How to create Kubernetes Secrets?
There are multiple ways, one can create Kubernetes Secrets and we will look at all of the various options.
Using Command-Line and Literal Input - Imperative Method
This is one of the imperative ways to create a secret. The command should like below.
kubectl create secret generic mysupersecret --from-literal=username=administrator --from-literal=password=Kubernetes1\!
Notice that we are providing the password in the literal form and if there are any special characters in the password, they should be preceded with \ to instruct kubectl about it.
Using Command-Line and Text Files - Imperative Method
The second imperative way is to create the secrets using the text files as input for each of the key-value pairs.
We will first run the below commands to add the details of the username and password into two files.
echo -n 'administrator' > username
echo -n 'Kubernetes1!' > password
We can now create the secret using the below command.
kubectl create secret generic mysupersecret --from-file=username --from-file=password
Using Base64 and Data Parameter - Declarative Method
As always mentioned, we should the declarative method as much as possible and this is the first method where we can create the secret using Base64 encoded data into the yaml file.
echo -n 'administrator' | base64
YWRtaW5pc3RyYXRvcg==echo -n 'Kubernetes1!' | base64
S3ViZXJuZXRlczEh
The above commands will generate the encoded values that we can now use in the yaml file. The final yaml file will look like below.
apiVersion: v1 kind: Secret metadata: name: mysupersecret type: Opaque data: username: YWRtaW5pc3RyYXRvcg== password: S3ViZXJuZXRlczEh
Now we can use kubectl command to create the secret.
kubectl create -f my-supersecret.yaml
Using Text and StringData Parameter - Declarative Method
The final way to creating a secret is using the declarative method is using the StringData parameter in the yaml file.
In the previous example, we encoded the clear text information and then provided it to Kubernetes to create the secret.
In this method, Kubernetes will encode it for us as part of creating the secret and we can provide the information in clear text format.
apiVersion: v1 kind: Secret metadata: name: mysupersecret type: Opaque stringData: superuser: 'administrator' password: 'Kubernetes1!'
We can create the secret using the kubectl command.
kubectl create -f my-supersecret.yaml
How to use the secret inside the Pods?
As you can imagine, we can now in one of three ways inside the pods as we did for Kubernetes ConfigMaps.
All keys as Environment Variables
The yaml file for this will look like.
apiVersion: v1
kind: Pod
metadata:
name: my-secret-pod
spec:
containers:
- image: busybox
name: busybox-container
command: ["sh" , "-c" , "echo The username is $(username) and the password is $(password)"]
envFrom:
- secretRef:
name: mysupersecret
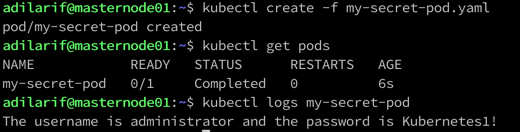
This is a simple busybox container in the pod which is going to print the username and password on the screen.
The commands used to create and check the output are:
kubectl create -f my-secret-pod.yaml
kubectl get pods
kubectl logs my-secret-pod
One or more keys are environment variables
The yaml file for this example is going to look like.
apiVersion: v1
kind: Pod
metadata:
name: my-secret-pod
spec:
containers:
- image: busybox
name: busybox-container
command: ["sh" , "-c" , "echo The username is $(username) and the password is $(password)"]
env:
- name: username
valueFrom:
secretKeyRef:
name: mysupersecret
key: username
- name: password
valueFrom:
secretKeyRef:
name: mysupersecret
key: password
The output of this going to be the same as above. This is just showing a different way to use the secrets within the pod.
Mount as volume
The yaml file for this example is going to look like.
apiVersion: v1
kind: Pod
metadata:
name: my-secret-pod
spec:
containers:
- image: nginx
name: nginx-container
volumeMounts:
- name: secret-volume
mountPath: /etc/config
volumes:
- name: secret-volume
secret:
secretName: mysupersecret
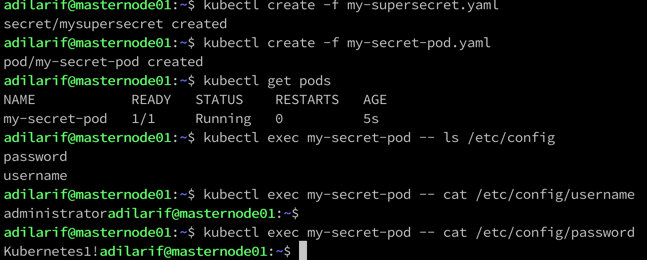
To create the pod and list the contents of the volume, the commands are below.
kubectl create -f my-secret-pod.yaml
kubectl get pods
kubectl exec my-secret-pod -- ls /etc/config
kubectl exec my-secret-pod -- cat /etc/config/username
kubectl exec my-secret-pod -- cat /etc/config/password
In the next post, we will discuss security contexts. I hope this has been informative and thank you for reading!